 Do you provide legal services to health care providers, health insurers, or health care clearinghouses? Do your clients support health care entities? In the course of representation, do you use, disclose, create, access, transmit, or maintain health information? If so, keep reading. You may now be subject to expanded liability under the Health Insurance Portability and Accountability Act of 1996 (HIPAA), the Health Information Technology for Economic and Clinical Health Act (HITECH Act), and these acts’ implementing regulations.
Do you provide legal services to health care providers, health insurers, or health care clearinghouses? Do your clients support health care entities? In the course of representation, do you use, disclose, create, access, transmit, or maintain health information? If so, keep reading. You may now be subject to expanded liability under the Health Insurance Portability and Accountability Act of 1996 (HIPAA), the Health Information Technology for Economic and Clinical Health Act (HITECH Act), and these acts’ implementing regulations.
It is important for lawyers1 to take note of the new changes to the HIPAA landscape, even lawyers who generally practice outside of the health law field. Lawyers in many areas – labor and employment, litigation, corporate, banking – may be subject to new, expanded liability as a result of the recently released omnibus final rule.
On Jan. 25, 2013, the U.S. Department of Health and Human Services Office for Civil Rights (OCR) published the omnibus final rule to implement changes to the HIPAA privacy, security, and breach notification rules (Omnibus Rule).2 The Omnibus Rule was highly anticipated and an exciting read for lawyers who focus on health law and privacy law, but the rule landed largely unnoticed by many lawyers in other practice areas. This article will help any attorney who deals with health information understand the new changes and what the changes might mean for his or her law practice.
Why Does It Matter Now?
HIPAA requires covered entities – including health care providers, insurers, and health care clearinghouses – to protect the privacy, confidentiality, and security of health information. HIPAA dictates how covered entities may use and disclose “protected health information” (commonly known as PHI but hereinafter referred to as health information),3 as shown in Figure 1: Protected Health Information: It’s More Than What You Think. When covered entities share health information with their business associates, including their lawyers, covered entities must enter into business-associate agreements (commonly known as BA agreements or BAAs) that hold business associates contractually responsible for protecting the privacy and security of health information.4
 Meghan O’Connor, Marquette 2010, is a member of the health care and government and regulatory law sections at von Briesen & Roper S.C., Milwaukee. Her practice focuses on regulatory compliance, HIPAA, and other federal and state privacy law, managed care and provider contracting, general corporate, business transactions, and risk management. She previously worked for the U.S. Department of Health and Human Services, Centers for Medicare and Medicaid Services.
Meghan O’Connor, Marquette 2010, is a member of the health care and government and regulatory law sections at von Briesen & Roper S.C., Milwaukee. Her practice focuses on regulatory compliance, HIPAA, and other federal and state privacy law, managed care and provider contracting, general corporate, business transactions, and risk management. She previously worked for the U.S. Department of Health and Human Services, Centers for Medicare and Medicaid Services.
 Diane M. Welsh, American Univ. 1998, is a shareholder at von Briesen & Roper S.C., Madison. Her practice includes litigation, health care, government law, regulatory matters, and crisis management. She focuses, in part, on HIPAA and other federal and state privacy laws. She previously was chief legal counsel for the Wisconsin Department of Health Services and an assistant attorney general at the Wisconsin Department of Justice.
Diane M. Welsh, American Univ. 1998, is a shareholder at von Briesen & Roper S.C., Madison. Her practice includes litigation, health care, government law, regulatory matters, and crisis management. She focuses, in part, on HIPAA and other federal and state privacy laws. She previously was chief legal counsel for the Wisconsin Department of Health Services and an assistant attorney general at the Wisconsin Department of Justice.
Although the HITECH Act required lawyers to comply with several privacy and security requirements beginning in 2009, the Omnibus Rule’s expanded liability has increased the scope of requirements for lawyers and the probability of enforcement by the federal government.
Before passage of the Omnibus Rule, business-associate liability was limited to contractual obligations to comply with BA agreement terms. However, under the Omnibus Rule, contractual liability is not all that business associates must consider; the OCR now has direct enforcement authority over business associates and their subcontractors5 for certain alleged HIPAA violations.6
Who is a Business Associate?
Because the Omnibus Rule includes significant changes and consequences for business associates, the question of whether a lawyer is a business associate is crucial to the scope of privacy and security compliance requirements.
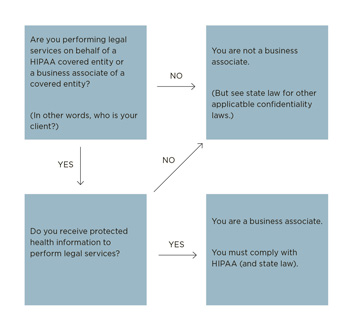
The Omnibus Rule expands the definition of a business associate to include persons or entities – other than members of the covered entity’s workforce – who create, receive, maintain, or transmit health information on behalf of a covered entity. The Omnibus Rule also expressly revised the definition of business associate to include subcontractors of business associates (more on subcontractors below). See Figure 2: Are You a Business Associate?
Lawyers who work for or on behalf of a covered entity or business associate, and who use health information to perform that work, fall squarely within that definition. The Omnibus Rule establishes that a person or organization becomes a business associate by definition, not by the act of executing a BA agreement with a covered entity.7 This means that lawyers are not immune from HIPAA business-associate liability even if they have failed to enter into BA agreements with their clients.
In other words, if an attorney represents a covered entity, and the work requires access to health information, the attorney is a business associate.
Not all lawyers who use health information are covered by HIPAA. Notably, a lawyer is not acting as a HIPAA-covered business associate or subcontractor when the lawyer is representing an individual or organization that is neither a HIPAA-covered entity nor a business associate – even if the lawyer is using health information. For example, a family-law practitioner, employment attorney, or defense attorney might need to access, use, or disclose health information. The health information will likely be accessed by way of an authorization form, the statutory provision that allows for use of health records for worker’s compensation matters,8 or court order.
Figure 1
Protected Health Information: It’s More Than What You Think
Individually identifiable health information is information, including demographic information, that relates to:
- The individual’s past, present, or future physical or mental health condition;
- The provision of health care to the individual; or
- The past, present, or future payment for the provision of health care to the individual
and that identifies the individual, or for which there is a reasonable basis to believe, can be used to identify the individual.
The following 18 types of information make individually identifiable health information PHI, and all 18 must be removed to make health information “de-identified” and not subject to HIPAA:
- Name
- Address (geographic subdivisions smaller than a state)
- Email address
- Dates (except years) – birth date, admission/discharge dates
- Telephone numbers
- Fax numbers
- Social Security number
- Medical record number
- Health plan beneficiary number
- Account numbers
- Certificate/license numbers
- Vehicle identifiers and serial numbers, including license plate numbers
- Device identifiers and serial numbers
- URLs
- IP addresses
- Biometric identifiers, including finger and voice prints
- Full-face photographic images and any comparable images
- Any other unique identifying number, characteristic, or code
See 45 C.F.R. §§ 160.103, 164.514.
If the lawyer is not acting as a business associate of a covered entity or another business associate, then the OCR would not have enforcement authority over the attorney for HIPAA compliance. Nonetheless, lawyers should be knowledgeable about HIPAA requirements for accessing and protecting health information. Moreover, Wis. Stat. sections 51.30 and 146.82 create legal obligations to properly use and limit disclosure of any health information received during the course of representation.
What are the Obligations of a Business Associate?
Lawyers who fit within the definition of a business associate must meet requirements of the HIPAA rules, including certain privacy, security, and breach-notification rule requirements. Significant requirements and considerations for lawyers and law firms are discussed below.
Privacy Rule Compliance. HIPAA outlines specific requirements for the use and disclosure of health information.9 Lawyers must only use and disclose health information as permitted by law or pursuant to patient authorization. They must ensure that the health information they request, use, and disclose is limited to the minimum amount of health information necessary to accomplish the purpose of the request, use, and disclosure.10
In the legal field, considerations include, for example, whether 1) document-management programs can limit the searchable nature of and access to records containing health information once matters have been closed; and 2) documents containing health information from an old matter are used as templates in unrelated matters.
In addition, law firms must be able to demonstrate that their workforce members (for example, lawyers, paralegals, support staff, information technology employees, interns, and law clerks) who have access to health information have been appropriately and timely trained on HIPAA compliance.11
Security Rule Compliance. Lawyers must be able to demonstrate implementation of appropriate safeguards (physical, administrative, and technical) to protect the confidentiality, integrity, and availability of health information that is maintained electronically.12 Lawyers should complete and document a risk assessment of the risks and vulnerabilities of their information systems (for example, document-management systems and client databases) and implement a risk-management program to reduce such risks and vulnerabilities.13 One standard that law firms should address is their ability to encrypt data containing health information.1414
Policies and Procedures. To comply with HIPAA, lawyers should develop a full set of policies and procedures that appropriately address specific privacy and security considerations.15 Law firms need to designate HIPAA security and privacy officials responsible for the implementation of policies and procedures and HIPAA compliance.16
Tracking and Monitoring Data. Lawyers must be able to provide covered-entity and business-associate clients with a full list of the uses and disclosures of health information if the uses or disclosures were made 1) beyond the scope of the patient’s authorization (if applicable); or 2) for a purpose other than the health-care-entity client’s payment or health-care-operations activities.17 Lawyers should ensure that their staff and systems can track each disclosure.
Breach Notification. Lawyers must be prepared to notify their health care clients if any unsecured health information is used, disclosed, accessed, or acquired in violation of HIPAA privacy or security rule requirements.18 In a law practice, a breach could occur when an unencrypted laptop is stolen, a firm mobile phone is lost, an unencrypted email is intercepted or misdirected (including when lawyers email documents to their personal email addresses to work at home), the law firm’s IT system is hacked, or paper files containing health information are lost or misplaced.19 Each of these occurrences must be reported to covered-entity and business-associate clients and appropriately mitigated.20
Figure 2
Are You a Business Associate
Breaches can lead to serious consequences, including investigation, fines, mitigation costs, and reputational harm. Covered entities must notify the U.S. Department of Health and Human Services (HHS) of any breach of unsecured health information (including by a business associate). The covered entity also must report to the media breaches involving more than 500 individuals.
Subcontractors. The federal government has indicated that it may hold business associates vicariously liable for the HIPAA violations of their subcontractors based on an analysis of the parties’ relationship using the federal common law of agency.21 The analysis is fact based, taking into account the terms of the BA agreement and the ongoing relationship of the parties, including the extent to which one party has the right or authority to control the other party’s conduct.22
This is a particularly important change for lawyers who coordinate or contract with independent contractors to provide services to clients (for example, document-management and other information-system contractors, shredding companies, and expert witnesses).23
Enter into BA Agreements. Lawyers who fall under the definition of a business associate or subcontractor have an obligation to enter into BA agreements with any clients or contractors that create a business-associate relationship. Any existing BA agreements that were entered into before the Omnibus Rule went into effect must now be updated with Omnibus Rule requirements.24
Return, Destroy, or Maintain Health Information. When the business-associate relationship between lawyers and covered entities ends, lawyers must return or destroy all health information received by the lawyer (and any of its subcontractors) from or on behalf of the covered entity.25 If returning or destroying health information is not feasible – which is often true for lawyers – lawyers must extend HIPAA protections of the health information for so long as the lawyer maintains the health information.26 Consequently, lawyers should be prepared to maintain privacy and security protections indefinitely or for as long as health information is maintained.
Risks as a Business Associate
Lawyers who are business associates face new risks, including the OCR’s new mandatory investigatory authority and direct enforcement authority over business associates, the potential for criminal and civil money penalties, and public relations considerations.
Because the Omnibus Rule expands the OCR’s ability and obligation to investigate alleged HIPAA violations and enforce HIPAA requirements directly against business associates, business associates are now subject to both OCR audits and investigations.27 Previously, the OCR had permissive investigatory authority, but the Omnibus Rule now mandates that the OCR formally investigate any complaint if a preliminary investigation of the facts indicates a possible HIPAA violation caused by willful neglect.28
Figure 3
Penalties of HIPAA Violations
Violation Category |
Civil Money Penalty for Each Violation |
Violations of an Identical Provision in Calendar Year |
|---|
Entity did not know and by exercising reasonable diligence, would not have known that it violated the applicable provision |
$100 to $50,000 |
$1,500,000 |
Violation due to reasonable cause and not willful neglect |
$1,000 to $50,000 |
$1,500,000 |
Violation due to willful neglect and was corrected during 30-day cure period beginning on the first day the entity knew or by exercising reasonable diligence, would have known that the violation occurred |
$10,000 to $50,000 |
$1,500,000 |
Violation due to willful neglect and was not corrected during 30-day cure period |
$50,000 or more |
$1,500,000 |
If the OCR determines there has been a violation of HIPAA, the OCR is now permitted to resolve the matter through an informal process or move directly to a formal process, including the imposition of penalties, without first exhausting informal resolution efforts.29 These penalties can be significant.30 Penalties may be imposed regardless of whether a BA agreement is in place.31 See Figure 3: Penalties of HIPAA Violations.
Lawyers should consider the reputational harm that would likely result from a HIPAA violation or enforcement action. Health care entities take their responsibility to safeguard health information very seriously. A breach by an entity’s lawyer will also implicate the covered entity through the required notice to the HHS and affected individuals. Moreover, breaches of health care information often are well publicized in trade publications and the popular press.
Fortunately, protecting the privacy of information is something that lawyers have been trained to do. And, the obligation to maintain the privacy and security of health information is consistent with a lawyer’s obligation to maintain the confidentiality of information relating to the representation of a client under Wisconsin Supreme Court Rule (SCR) 20:1.6.32 However, the responsibilities under HIPAA are broader and more proscriptive than those of SCR 20:1.6.
Where to Begin? At the Beginning, of Course
If a firm has determined that it is a business associate covered by HIPAA, then the firm should start by determining if it is able to comply with the HIPAA privacy and security rules. The firm should conduct a gap analysis, comparing the rules against the firm’s current policies, procedures, and practices.
The analysis should include an assessment of the firm’s security compliance capabilities, examining its technical, administrative, and physical safeguards. Review whether the IT department (or contractor) is up to snuff and able to help ensure compliance. The firm should also assess its capabilities to use encryption and de-identification to protect health information.
Law firms must also enter into BA agreements, with covered-entity and business-associate clients and with subcontractors, that include applicable privacy and security-rule provisions. These BA agreements should clearly specify authorized uses and disclosures of health information, outline the relationship between the parties, address applicable privacy and security requirements, and document the lawyer’s return-or-destroy obligations.33
Existing BA agreements between law firms and clients or subcontractors must be updated and compliant with Omnibus Rule provisions by Sept. 22, 2014.34 For firms that do not currently have BA agreements with covered-entity and business-associate clients and subcontractors, new BA agreements should be put in place now. Compliance with new requirements is necessary by Sept. 22, 2013.
In addition, law firms should be prepared to present documentation regarding efforts to maintain an active and robust compliance program and appropriate organizational responses to HIPAA violations. To accomplish this, firms should do the following:
- Create or update HIPAA compliance plans, policies, and procedures. Areas covered should include IT, privacy, security, access, and breach notification policies and procedures.
- Develop a team that can appropriately respond to breaches and security incidents.
- Conduct workforce training.
Conclusion
Share Your Thoughts!
State Bar members can comment on the article in the box at the bottom of the page. If you haven't already, login and join the conversation.
Any lawyer who works with health information should take proactive steps to remain in – or come into – compliance with HIPAA. Doing so will be an expectation of your clients and will help prevent unintentional breaches. These steps will also protect lawyers against enforcement actions, negative audit findings, or damage to professional reputations.
Because of the general nature of this article, the information provided may not be applicable to all situations and should not be acted on without specific legal advice based on particular circumstances.
Endnotes
1 We use the terms “lawyers” and “law firms” throughout this article. These terms apply to lawyers in any size practice, from solo practitioner to large firm, as well as governmental legal offices. Under the Omnibus Rule, any person, including a natural person, partnership, corporation, or other entity, public or private, may be a business associate under HIPAA. See 78 Fed. Reg. 5598 (Jan. 25, 2013).
2 The full name of the Omnibus Rule is: Modifications to the HIPAA Privacy, Security, Enforcement and Breach Notification Rules under the Health Information Technology for Economic and Clinical Health Act and the Genetic Information Nondiscrimination Act; Other Modifications to the HIPAA Rules. 78 Fed. Reg. 5566 (Jan. 25, 2013). The Omnibus Rule took effect on March 26, 2013, and the compliance date is Sept. 23, 2013, when covered entities and business associates must be in compliance with a majority of the Omnibus Rule provisions.
3 See, e.g., 45 C.F.R. §164.502 (general rules on use and disclosure of PHI); see 45 C.F.R. §160.103 (definitions of covered entity, business associate, and protected health information).
4 See 45 C.F.R. § 164.504(e).
5 A subcontractor is a person or entity to whom a business associate delegates a function, activity, or service, other than in the capacity of a member of the workforce of such business associate. 45 C.F.R. § 160.103.
6 See 78 Fed. Reg. 5573, 5589, 5591, 5598, 5601.
7 See 78 Fed. Reg. 5599.
8 Worker’s compensation matters fall under Wis. Stat. sections 102.13(2)(a) and 102.33. When an employee files a worker’s compensation claim, the employee waives provider-patient privilege with regard to health information (that is, any condition or complaint) reasonably related to the condition for which the employee is claiming compensation. This waiver of provider-patient privilege includes health information subject to protections of Wis. Stat. sections 51.30 and 146.82, but only to the extent such health information is related to the condition for which the employee is claiming compensation. Despite waiving provider-patient privilege, the employee does not waive HIPAA requirements. This means that, among other requirements, when handling a worker’s compensation matter, attorneys should expect that they will have access to only the information related to the worker’s compensation claim.
9 See, e.g., 45 C.F.R. §§ 164.502, 164.506, 164.508, 164.510, 164.512, 164.514.
10 45 C.F.R. § 164.502(b).
11 45 C.F.R. §§ 164.308(a)(5), 164.530(b).
12 45 C.F.R. §§ 164.306(a), 164.308, 164.310, 164.312.
13 45 C.F.R. § 164.308(a)(1)(ii)(A)-(B).
14 45 C.F.R. §§ 164.304, 164.312(2)(iv); 78 Fed. Reg. 5671, 5682, 5644. The OCR has outlined its interest in encryption several times. According to OCR director Leon Rodriguez, “Encryption is an easy method for making lost information unusable, unreadable and undecipherable.” Press Release, U.S. Department of Health & Human Services, HHS announces first HIPAA breach settlement involving less than 500 patients (Jan. 2, 2013), available at www.hhs.gov/news/press/2013pres/01/20130102a.html.
15 45 C.F.R. § 164.316.
16 45 C.F.R. §§ 164.308(a)(2), 164.530(a)(1).
17 45 C.F.R. § 164.528.
18 An acquisition, access, use, or disclosure of protected health information in a manner not permitted under the HIPAA privacy rule (45 C.F.R. pt. E) and that compromises the security or privacy of the PHI is presumed to be a breach unless the entity can demonstrate a low probability that the PHI was compromised. See 45 C.F.R. § 164.402. To determine whether the security or privacy of the PHI has been compromised, the Omnibus Rule requires an assessment of a minimum of four factors outlined in 45 C.F.R. section 164.402. See also 45 C.F.R. § 164.410 (business associate breach notification requirements).
19 A security incident is an attempted or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with system operations in an information system. 45 C.F.R. § 164.304.
20 See 45 C.F.R. §§ 164.410, 164.503(f).
21 45 C.F.R. § 160.402(c); see 78 Fed. Reg. 5572-73, 5598, 5677.
22 78 Fed. Reg. 5581.
23 For a discussion of a shredding company, see 78 Fed. Reg. 5573.
24 See 45 C.F.R. §§ 164.504(e)(2)(ii)(B)-(D), 164.504(e)(2)(ii)(H); see also 78 Fed. Reg. 5600.
25 45 C.F.R. § 164.504(e)(2)(i)(J).
26 Id.
27 45 C.F.R. § 160.308; 78 Fed. Reg. 5578.
28 45 C.F.R. § 160.306(c)(1); 78 Fed. Reg. 5578.
29 45 C.F.R. § 160.302(a); 78 Fed. Reg. 5578.
30 45 C.F.R. § 160.404. See 78 Fed. Reg. 5583-86 for a discussion of how violations are calculated and the factors considered in determining the amount of CMPs. See also 42 U.S.C. § 1320d-6 for criminal penalties.
31 78 Fed. Reg. 5599.
32 SCR 20:1.6.
33 See 78 Fed. Reg. 5601.
34 However, if the scope of engagement between the firm and covered entity or business associate clients changes before Sept. 22, 2014, an updated BA agreement must be put into place with the new engagement letter.
